Endpoint data loss prevention (DLP)
It’s easy for sensitive information on endpoint computers to escape your organization through peripheral devices, local interfaces, and various network channels. Data leaks can lead to severe financial and reputational damage, loss of trade secrets, and expensive regulatory fines and litigation. To prevent leakage due to employee negligence or malicious insiders, you need data loss prevention (DLP) capabilities that block any unauthorized attempts to transfer sensitive data.
Stop data leaks at the source with complete endpoint DLP
Acronis DeviceLock DLP provides comprehensive endpoint DLP – discovering and protecting sensitive data while monitoring the operations involving that information.
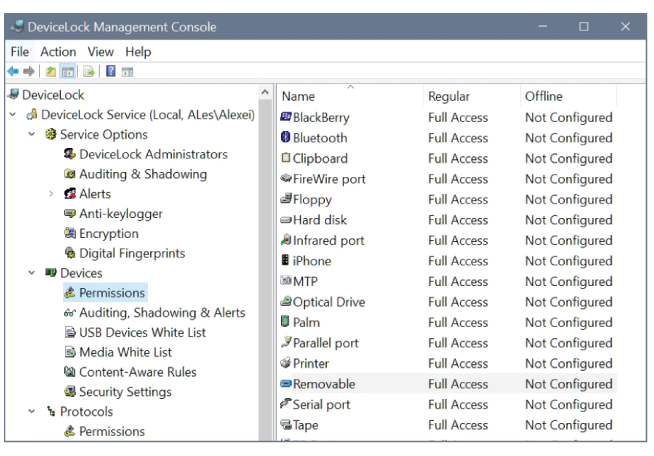
Block unauthorized device and network access
Proactively prevent data leakage by allowing access only to devices, peripherals, and network communication channels such as email, instant messengers, and social media, that are required for business operations. Block access to unauthorized local and network channels on corporate computers. Enable business operability by specifying whether protected endpoints may only receive data via the controlled channels (read-only/receive-only) or if they may also use it for data transfers.
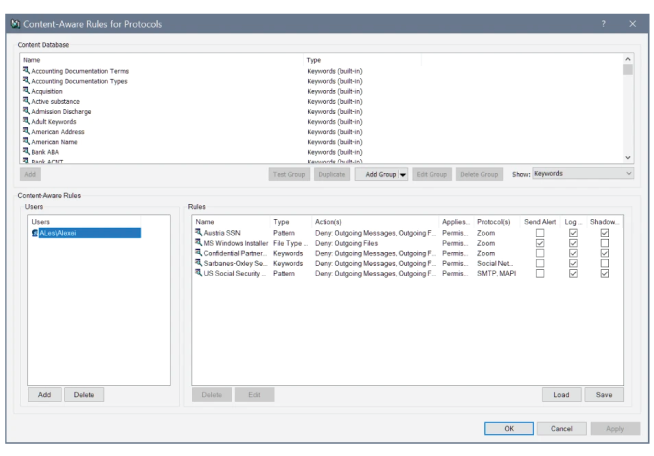
Comprehensive control of outgoing network communications
Reduce the risk of sensitive data leaving your company through network channels (plain or SSL-encrypted communication) by applying context- and content-based controls to outgoing messages, attachments, and file uploads.
Emails and webmails
Apply granular DLP controls to outgoing
emails and attachments, including text
recognition in inline images, and attached graphical files. Allow communication only via specific mail services or from and to particular email addresses. Restrict users’ ability to send
email attachments.
Collaboration and messaging tools
A unique technology allows you to control the content of files and messages transferred via instant messengers such as Skype, Zoom, or
Viber. You can even allow or deny communication between specific users, including media calls.
Social media
Control access to social media and apply content-aware DLP controls when sending messages, comments, posts, or uploading files, including text recognition in images. Allow users to access social media in “view-only” mode, to ensure no leakage of sensitive information.
Don’t let any sensitive data escape your organization with granular DLP controls
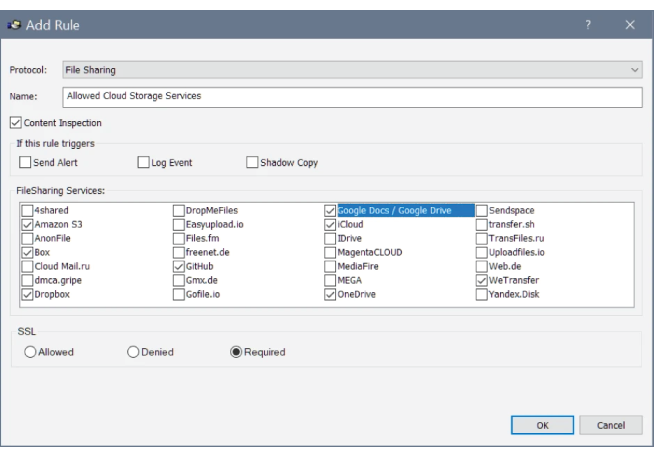
Control sensitive data transfer to cloud file storage
Ensure users are allowed to perform only operations necessary for the business across cloud file storage platforms. Allow or deny access to specific cloud file storage and apply context- and content-based controls to both uploaded files and comments, including text recognition in images. Restrict the access permissions for specific users or groups to download-only to effectively prevent data leaks.
Control clipboard usage and screenshot captures
Prevent data leaks at their earliest stage – when data is copied or transferred via the clipboard. Selectively allow or deny the copying of specific data types or content within an application or between them. Control PrintScreen usage or third-party screenshot capturing tools. Restrict operations based on the textual content detected in copied images with a built-in optical character recognition technology.
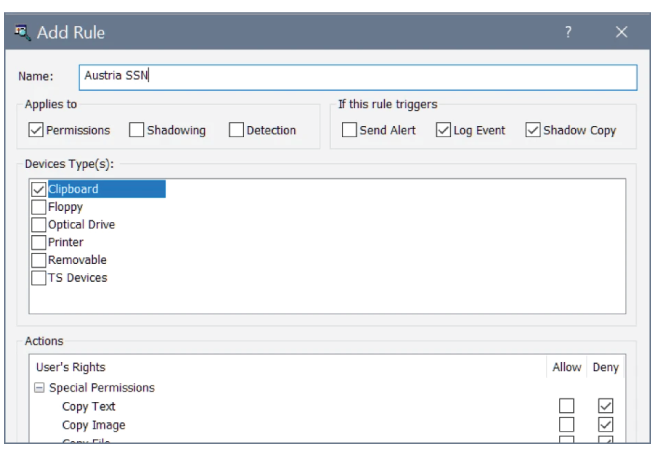
Limit data copying only to secure removable media
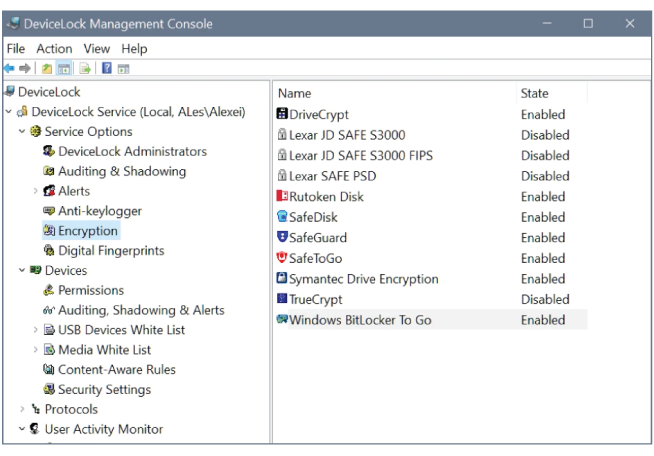
Neutralize one of the primary vectors of data leakage — uncontrolled use of removable media, which enables stealthy exfiltration of data from corporate endpoints. Allow users to safely copy data only to specific, company-approved USB devices, including ones protected with third-party software or hardware encryption.
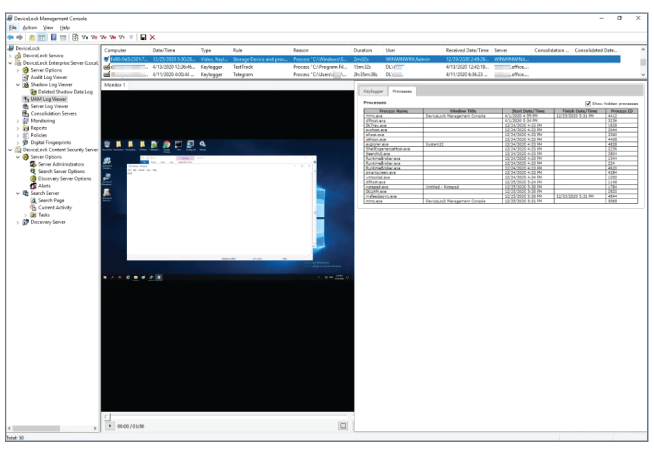
Enable security investigations with user activity monitoring (UAM)
Expand your evidence base for security incident investigations and simplify the detection of access privilege misuse by recording user activity based on system state, or DLP policy violations. Record the user’s computer screen together with on-screen actions, keystrokes, and information about applications that were used on the computer during recording, and store it in a central DLP log database for analysis.
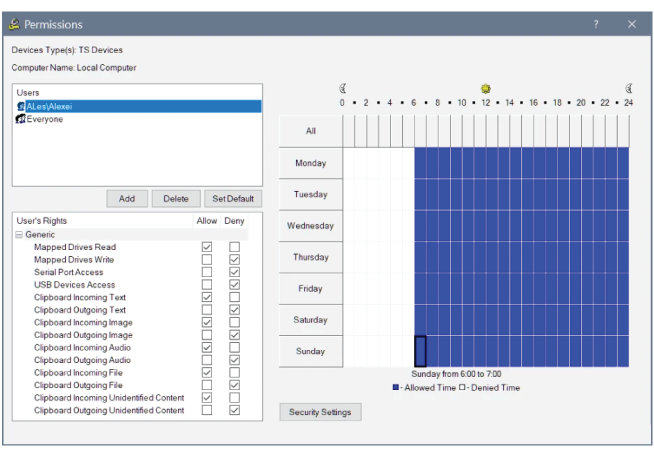
Prevent data leaks in remote desktop sessions
Remote virtualization solutions can be used by employees to access business systems via remote terminals or BYOD devices. If data flows between desktop sessions and peripherals redirected from remote terminals aren’t controlled, users can easily transfer data from virtual corporate desktops to their personal devices. With Acronis DeviceLock DLP, you can restrict data flows from centrally hosted virtual desktops and applications to remote terminals and BYODs only when it is needed for the business, while blocking any unnecessary outgoing data transfers — proactively preventing data leakage.
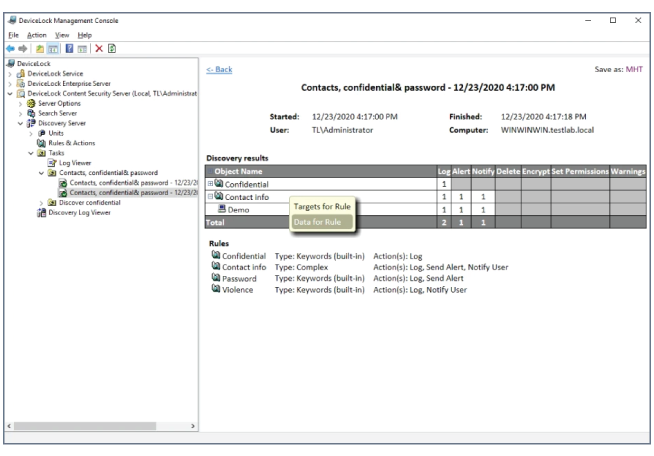
Proactively protect data at rest across the organization
Find exposed sensitive content stored across the organization (corporate endpoints, network attached storage systems, file shares, Elasticsearch databases) and protect it with automatic, configurable remediation actions. Gain visibility and control over confidential “data at-rest” stored across the IT environment for proactive data loss prevention and increased compliance with regulatory and corporate data security requirements.